Autonomous Build Network: Distributing Software Supply Chain for Build Integrity
What is Autonomous Build Network? (TL;DR)
Autonomous Build Network (ABN) establishes build system security through transparency and integrity. By using a reproducible and bootstrapped process it allows each builder to verify the integrity of their process. Combined with a distributed attestation network, ABN delivers a strong integrity guarantee, eliminating the need to place trust in any single compiler, toolchain, builder, or host.
This is the core idea behind our project. Before going further, I’d like to take a step back and explain the reasoning behind our focus on this particular field.
The Core Problem with Current Software Distribution
Modern software distribution faces critical security challenges rooted in complexity, opacity, and centralization. Most software today depends heavily on external libraries and third-party components, often integrated with minimal scrutiny. Insider threats, whether malicious or accidental, further compromise trust in the supply chain. This creates multiple attack vectors: compromised build environments, malicious package maintainers, or infrastructure breaches. These are just a few sources of vulnerabilities or backdoors in software that users depend on. Meanwhile, the sheer volume of discovered vulnerabilities, combined with the need to balance security updates frequency and system stability, makes effective vulnerability management a persistent struggle.
There are multiple ways to address these issues, including securing build and deployment environments, enforcing strict dependency controls, applying robust access management, and isolating networks. While these measures greatly strengthen supply chain security, none can fully guarantee a secure software distribution. Decades of ad-hoc solutions and bad software provision practices made it practically impossible to trace the route of software distribution integrity. There is a need for verifiable methods to ensure that binaries accurately reflect their source code. Ken Thompson articulated this problem in his 1984 lecture Reflections on Trusting Trust, where he posed a critical question about the foundations of trust in software systems:
“No amount of source-level verification or scrutiny will protect you from using untrusted code.”
And yet, we believe there is a path forward. We can establish build integrity in software distribution by ensuring that binaries accurately reflect their source code. This requires rethinking and rebuilding our distribution processes, from the tiny bits upward, and bootstrapping transparent and secure systems. However, it will require significant advocacy and the adoption of new approaches. In light of today’s systemic risks and trust failures, it stands as the only credible path toward a secure and verifiable software ecosystem.
The Reproducible Build Process with Full Source Bootstrapping
We’re not the first to pursue this vision. Significant work has already been done in this area. The GNU Project began exploring the idea of reproducible builds as early as the early 1990s, and since then, others (NixOS, GNU Guix, GNU Mes) have continued work towards fully bootstrapped and verifiable environments. Reproducible Builds guarantee that compiling the same source code always results in identical binaries. This makes it possible to verify that the software hasn’t been altered, enhancing consistency, transparency, and trust. Meanwhile, Full Source Bootstrapping offers clear provenance by mapping out a full dependency graph, showing exactly how each binary was built and where it came from.
ABN adopts these approaches and turns into a distributed protocol. It works on the following principle: if multiple independent builders produce identical binaries from the same source code, we can be confident the build process is free from tampering or compromise. This principle forms the foundation of ABN’s distributed attestation network.
Distributed Attestation Network
The strength of ABN architecture lies in its distributed design — no single entity controls the build process. As a result, users aren’t required to trust any individual compiler, toolchain, builder, or host, effectively removing single points of trust. To better understand this concept, let’s take a closer look at how ABN operates at this level.
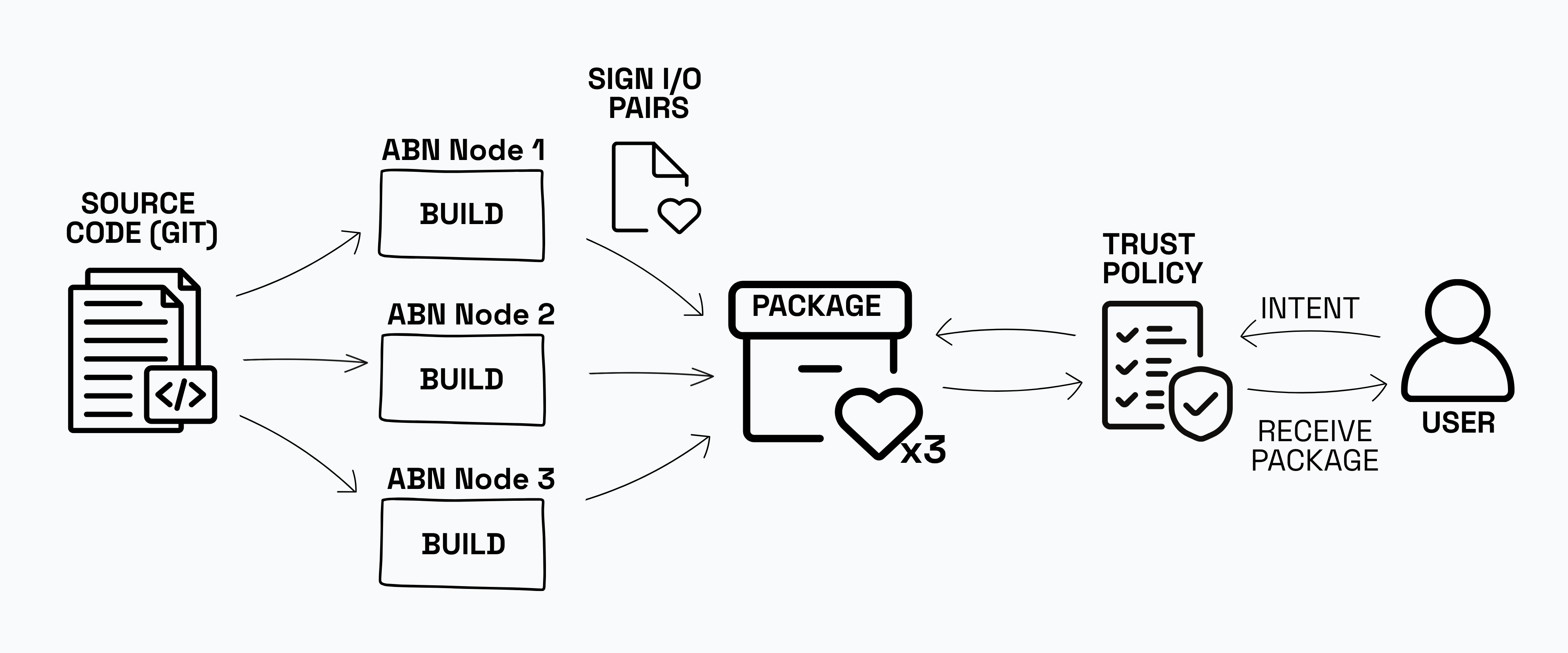
Packages in the ABN will be built in a reproducible manner from a bootstrapped set of binaries. Source code is fetched from repositories such as Git, and each ABN node independently builds the package and generates an attestation for its input-output hash pair. These hashes are then compared across nodes. If the builds are reproducible and free of bugs or malicious modifications, the resulting binaries will be identical. In that case, the package is jointly attested by all nodes that produced matching results.
Furthermore, users can define their own trust policies, such as requiring a minimum number of attestations or specifying a trusted set of builders. When a user submits a request with their desired package and trust policy, the system evaluates whether the existing attestations meet those requirements. If they are met, only then is the verified package is fetched.
As you can imagine, as the network grows, the number of attestations will also increase, each one adding an extra layer of verification and strengthening the overall security of the system. This is how ABN decentralizes the software supply chain: distributing the trust.
Key Features of ABN
Now the key question is: how do we bring this complex system together in a neat way? We have outlined an architecture that incorporates the following key features:
- Fully declarative infrastructure-as-code: Enables deployment of complex systems on targets that require reproducibility, like secure enclaves.
- Practical full-source deployment, with an option to have policy-based verifiable binary fetching.
- Streamlines the secure deployment of sensitive applications. Provides a toolkit for a reproducible one-click deployment solution across several targets.
- Build process transparency: Verifiable builds ensure complete provenance and traceability in the software supply chain.
- Scalable security: As software ecosystems grow, this network ensures security and reproducibility on a large scale.
Transparently Private: Scaling ABN for Confidential Computation
It’s important not to confuse transparency with a lack of privacy. These are not mutually exclusive. In fact, ABN makes it possible to build a framework that supports confidential computation, where the integrity of the process is transparent and verifiable, while the data itself remains private and protected. We believe this capability shouldn’t be a luxury or an afterthought.
Built on ABN’s secure infrastructure, this framework supports Trusted Execution Environments (TEEs), allowing users to submit computation requests that are executed confidentially within a TEE. Even though we know TEEs remain vulnerable to hardware and supply chain attacks, we are addressing these limitations by working toward Autonomous TEEs. While this article won’t go into those efforts, you can learn more in our Autonomous TEE article.
This capability can be integrated into a wide range of applications, such as DeFi platforms, settlement systems, or clearing houses, civic technology solutions, confidential AI enabling them to handle sensitive operations in a secure and verifiable manner.